Burp Suite is a very effective HTTP traffic analysis tool. Here are the steps to set up Burp Proxy for android virtual device: Go to Menu - System Settings - Wireless and Network - Click on More. Burp Suite is one of my favorite tools to use when performing a Web Penetration Test. The following is a step-by-step Burp Suite Tutorial. I will demonstrate how to properly configure and utilize many of Burp Suite's features. After reading this, you should be able to perform a thorough web penetration test. This will be the first in a.
Environment:
Windows 7 Professional Edition 64-bit
Install Burp
The feature we need is called interception, and the free edition comes with that feature. Go to Burp website, download the free edition, and run the downloaded file to install Burp Suite:
Install & setup Firefox Developer Edition
Somehow, I did not manage to make Burp work with Internet Explorer 11 or Chrome, I set up the proxy in IE, but it just does not pause at Burp when sending requests, and Chrome reuses the IE settings, it does not work either. So, let's use Firefox, I choose developer edition in this instance.
Step 1: Install Firefox Developer Edition;
Step 2: Go to options:
And then choose Advanced->Network->Settings:

In the Connection Settings dialog, change the settings as shown:
Click OK to finish setting the proxy. This makes Firefox uses Burp as proxy for sending and receiving HTTP packages.
Start using Burp
Step 1: Open up Burp:
As a matter of fact, we don't have other options except the ‘Temporary project'. In the next dialog, click Start Burp.
Step 2: Start debugging session with Firefox Developer Edition from Visual Studio:
Step 3: Fill in the form in your web page, and trigger the browser to send a POST request with the data:
Burp will grab the focus, and pause the request, you can modify the values of the form parameters by editing the inline data, and then click Forward, to send the request to IIS Express that activated by VS.
Step 4: You can add a break point in the controller action's body, to inspect the real data the ASP.NET app receives:
As you see, I typed a normal email address initially, and modified it with Burp, and the modified value finally reached the server side program.
This can be handy when I only want to test against the server side validation behavior, and I don't have to twist the front-end code like JavaScript to disable the validation at client side.
Other Issues
For some reasons, Firefox Developer Edition keeps sending requests to the following hosts:
And this is quite annoying as it interferes the testing a lot. Someone has reported the issue here. As a post suggests, the behavior can be disabled by following the below steps:
Step 1: Go to the option list by browsing ‘about:config'
Burp Suite Wordpress Download
Click the ‘I accept the risk!', and in the next page, type ‘captiv' in the search box:
In the left options, right click the ‘network.captive-portal-service.enabled', and in the context menu, choose Toggle. This will disable it. However, it seems not to work for me, Firefox just keeps doing it.
I finally solved it by defining new intercepting rules:
Unfortunately, these setting rules will be gone after you exit Burp, so you had better export them into an option file, and export them next time:
Thanks for reading, I will update once I find a better way to make use of it.
In this article we will learn to prosecute dictionary attack from BurpSuite. And we will try and crack the password ofDVWA Lab.
Burp Suite: Burp Suite is an integrated platform for performing security testing of web applications. Its various tools work seamlessly together to support the entire testing process, from initial mapping and analysis of an application's attack surface, through to finding and exploiting security vulnerabilities.
Burp gives you full control, letting you combine advanced manual techniques with state-of-the-art automation, to make your work faster, more effective, and more fun. Importantly, it gives us another way to manage our attacks as the alternative to metasploit.
To make Burp Suite work, firstly, we have to turn on manual proxy and for that go to the settings and choosePreferences.
Then select advanced option and further go to Network then select Settings.
Now, select Manual proxy Configuration
And this way your manual proxy will be active as you can see below too.
Now, on the other hand open DVWA and log into it using its default username and password.
Once you log in, click on Brute Force. And also make sure that security is low or medium.
When you click on brute force, it will ask you the username and password. Here, before giving username and password open burp suite and select Proxy tab and turn on interception by clicking on Interception is on/off tab.
As you turn on the interception, then give any password you like just so that the burp suite can capture it.
Send the captured material to the intruder by right clicking on the space and choosing Send to Intruder option or simply press ctrl + i
Now open the Intruder tab then select Positions tab and following will be visible:
Choose the Attack type as Cluster Bomb.
Now select username and password as shown below:
In the above image we have selected username and password that means we will need two dictionary files i.e. one for username and second for password.
So now, go to Payloads tab and the select 1 from Payload set (this ‘1' denotes the username file). Then click on Loadbutton and browse and select your dictionary file for username.
Now select 2 in the Payload set and again similar give the dictionary file for the password.
Now all you have to do is go to Intruder menu and select Start attack from the drop down menu.
Sit back and relax because now the burp suite will do its work and match the username and password and will give you the correct password and username. The moment it will find the correct value, it will change the value of length as shown:
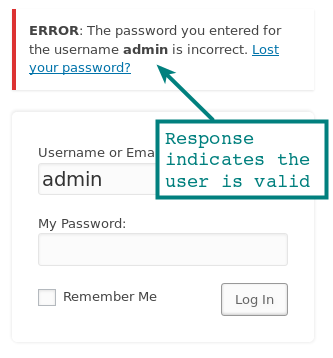
And to confirm it from the response as it will be 'Welcome to the password protected area admin'
And this way its all done.
Burp Suite Wordpress Themes
Shivam Gupta is An Ethical Hacker, Cyber Security Expert, Penetration Tester, India. you can contact here
Burp Suite Wordpress Login

Burp Suite is a very effective HTTP traffic analysis tool. Here are the steps to set up Burp Proxy for android virtual device: Go to Menu - System Settings - Wireless and Network - Click on More. Burp Suite is one of my favorite tools to use when performing a Web Penetration Test. The following is a step-by-step Burp Suite Tutorial. I will demonstrate how to properly configure and utilize many of Burp Suite's features. After reading this, you should be able to perform a thorough web penetration test. This will be the first in a.
Environment:
Windows 7 Professional Edition 64-bit
Install Burp
The feature we need is called interception, and the free edition comes with that feature. Go to Burp website, download the free edition, and run the downloaded file to install Burp Suite:
Install & setup Firefox Developer Edition
Somehow, I did not manage to make Burp work with Internet Explorer 11 or Chrome, I set up the proxy in IE, but it just does not pause at Burp when sending requests, and Chrome reuses the IE settings, it does not work either. So, let's use Firefox, I choose developer edition in this instance.
Step 1: Install Firefox Developer Edition;
Step 2: Go to options:
And then choose Advanced->Network->Settings:
In the Connection Settings dialog, change the settings as shown:
Click OK to finish setting the proxy. This makes Firefox uses Burp as proxy for sending and receiving HTTP packages.
Start using Burp
Step 1: Open up Burp:
As a matter of fact, we don't have other options except the ‘Temporary project'. In the next dialog, click Start Burp.
Step 2: Start debugging session with Firefox Developer Edition from Visual Studio:
Step 3: Fill in the form in your web page, and trigger the browser to send a POST request with the data:
Burp will grab the focus, and pause the request, you can modify the values of the form parameters by editing the inline data, and then click Forward, to send the request to IIS Express that activated by VS.
Step 4: You can add a break point in the controller action's body, to inspect the real data the ASP.NET app receives:
As you see, I typed a normal email address initially, and modified it with Burp, and the modified value finally reached the server side program.
This can be handy when I only want to test against the server side validation behavior, and I don't have to twist the front-end code like JavaScript to disable the validation at client side.
Other Issues
For some reasons, Firefox Developer Edition keeps sending requests to the following hosts:
And this is quite annoying as it interferes the testing a lot. Someone has reported the issue here. As a post suggests, the behavior can be disabled by following the below steps:
Step 1: Go to the option list by browsing ‘about:config'
Burp Suite Wordpress Download
Click the ‘I accept the risk!', and in the next page, type ‘captiv' in the search box:
In the left options, right click the ‘network.captive-portal-service.enabled', and in the context menu, choose Toggle. This will disable it. However, it seems not to work for me, Firefox just keeps doing it.
I finally solved it by defining new intercepting rules:
Unfortunately, these setting rules will be gone after you exit Burp, so you had better export them into an option file, and export them next time:
Thanks for reading, I will update once I find a better way to make use of it.
In this article we will learn to prosecute dictionary attack from BurpSuite. And we will try and crack the password ofDVWA Lab.
Burp Suite: Burp Suite is an integrated platform for performing security testing of web applications. Its various tools work seamlessly together to support the entire testing process, from initial mapping and analysis of an application's attack surface, through to finding and exploiting security vulnerabilities.
Burp gives you full control, letting you combine advanced manual techniques with state-of-the-art automation, to make your work faster, more effective, and more fun. Importantly, it gives us another way to manage our attacks as the alternative to metasploit.
To make Burp Suite work, firstly, we have to turn on manual proxy and for that go to the settings and choosePreferences.
Then select advanced option and further go to Network then select Settings.
Now, select Manual proxy Configuration
And this way your manual proxy will be active as you can see below too.
Now, on the other hand open DVWA and log into it using its default username and password.
Once you log in, click on Brute Force. And also make sure that security is low or medium.
When you click on brute force, it will ask you the username and password. Here, before giving username and password open burp suite and select Proxy tab and turn on interception by clicking on Interception is on/off tab.
As you turn on the interception, then give any password you like just so that the burp suite can capture it.
Send the captured material to the intruder by right clicking on the space and choosing Send to Intruder option or simply press ctrl + i
Now open the Intruder tab then select Positions tab and following will be visible:
Choose the Attack type as Cluster Bomb.
Now select username and password as shown below:
In the above image we have selected username and password that means we will need two dictionary files i.e. one for username and second for password.
So now, go to Payloads tab and the select 1 from Payload set (this ‘1' denotes the username file). Then click on Loadbutton and browse and select your dictionary file for username.
Now select 2 in the Payload set and again similar give the dictionary file for the password.
Now all you have to do is go to Intruder menu and select Start attack from the drop down menu.
Sit back and relax because now the burp suite will do its work and match the username and password and will give you the correct password and username. The moment it will find the correct value, it will change the value of length as shown:
And to confirm it from the response as it will be 'Welcome to the password protected area admin'
And this way its all done.
Burp Suite Wordpress Themes
Shivam Gupta is An Ethical Hacker, Cyber Security Expert, Penetration Tester, India. you can contact here
Burp Suite Wordpress Login
Burp Suite Wordpress Theme
[Souce] http://www.hackingarticles.in/brute-force-website-login-page-using-burpsuite-beginner-guide/
